Stable operation without downtime - including protection against cyber attacks
ControlTech Engineering AG (CTE) ensures that standards are maintained and benefits from 30 years of experience in operational technology (OT) infrastructure. Use our external resources for your fail-safe operation.
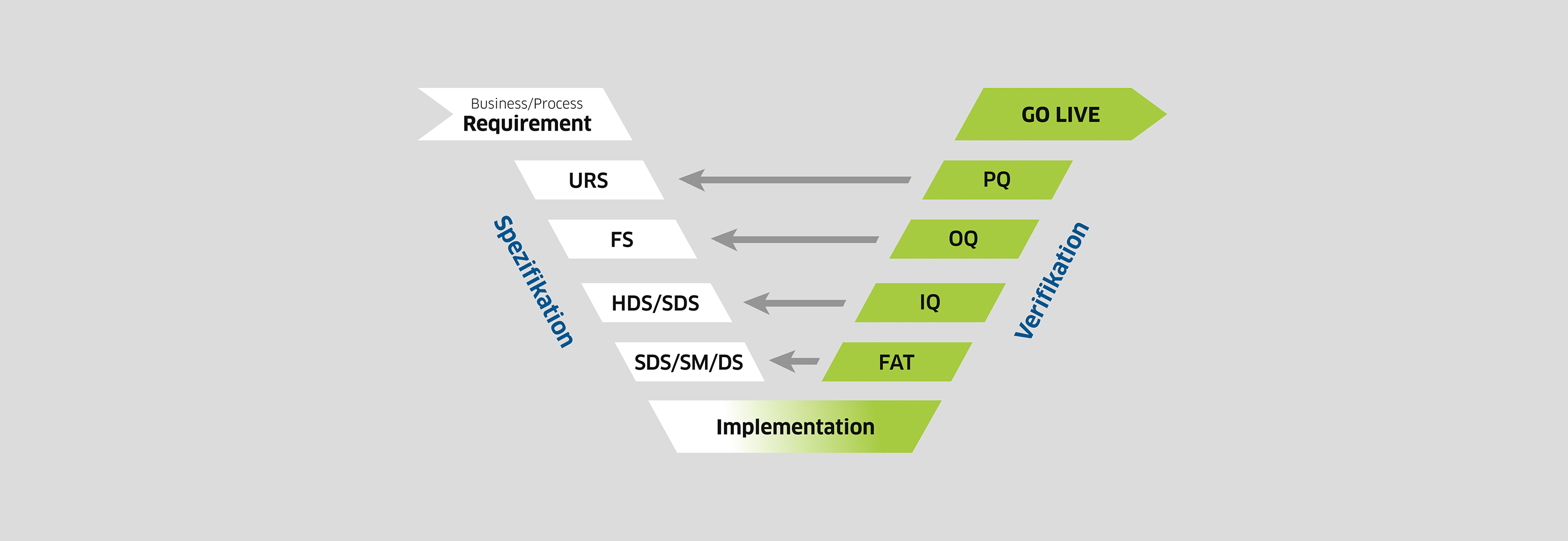
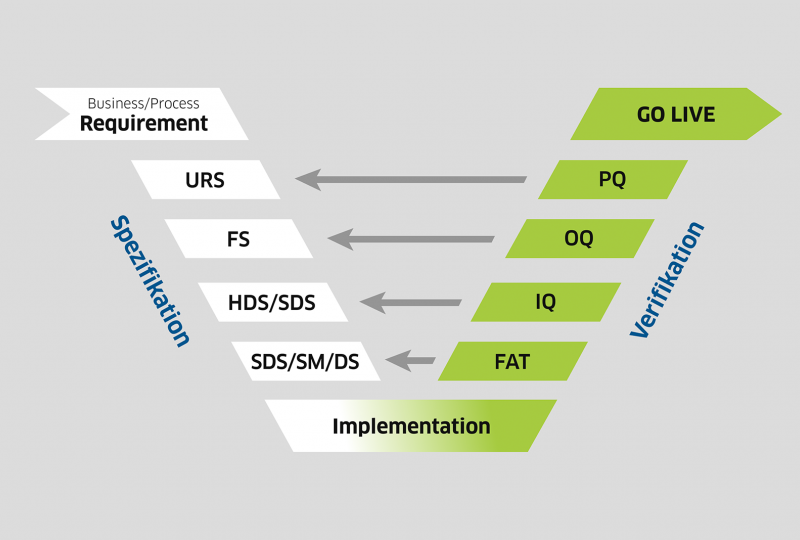
Regulatory requirements such as ISO 9001, ISO 45001, ISO 14001 or even ISO 27001 ensure a high level of bureaucracy. Heavy regulation from legislators such as NIS2 Kritis does not make your day-to-day operations any easier either. It is important to focus on the entire IT/OT infrastructure and always keep an eye on the strategy.
Your advantages at a glance
As experts in industrial IT, automation and data management, we are your regional partner for operational technologies (OT) and long-term support
Reliable forecasts based on reliable simulations help you to master daily challenges
A Vulnerability Scan identifies potential attack surfaces and subsequently ensures cyber security
With our security solutions, we ensure fail-safe production operations and the desired level of cyber security. As a regional partner, we can be on site quickly and provide close support with our more than 30 years of experience. Dealing with security tasks is part of our everyday work. That's why we proactively answer questions about updates to current technologies and protective measures. In the area of security, good preparation is everything. Minimizing risks with regard to regulations and cyber security helps you to ensure compliance. You can easily outsource regular security audits, backups, and access controls to us.
Safe, close-meshed, proactive - up and running!
Read more
A systematic assessment of your IT security risks ensures stable operations without outages and attacks. This increases your security and frees up your internal resources. We support you with detailed security requirements through automated assistance. This saves time and costs. You can focus on the strategy and do not have to concern yourself with the implementation down to the last detail.
In any case, a cyber incident causes significantly more effort and costs than preventive measures.