IEC 62443 - Orientation for more security in industrial IT
The IEC 62443 series of standards is considered the most important standard for industrial cyber security today. It provides companies with a clear framework for systematically securing production facilities and meeting regulatory requirements at the same time. But how can the standard be applied in practice - and where are individual adaptations necessary?
What is IEC 62443?
The IEC 62443 series of standards is the world's most important standard for cybersecurity in industrial automation and control systems (IACS). It is developed by the International Electrotechnical Commission (IEC) and has become a central reference framework in many industries, particularly in the process industry, the energy sector and manufacturing. The aim of the standard is to create a uniform foundation for safeguarding industrial systems, which traditionally have long life cycles and are often operated in environments in which availability and safety have the highest priority.
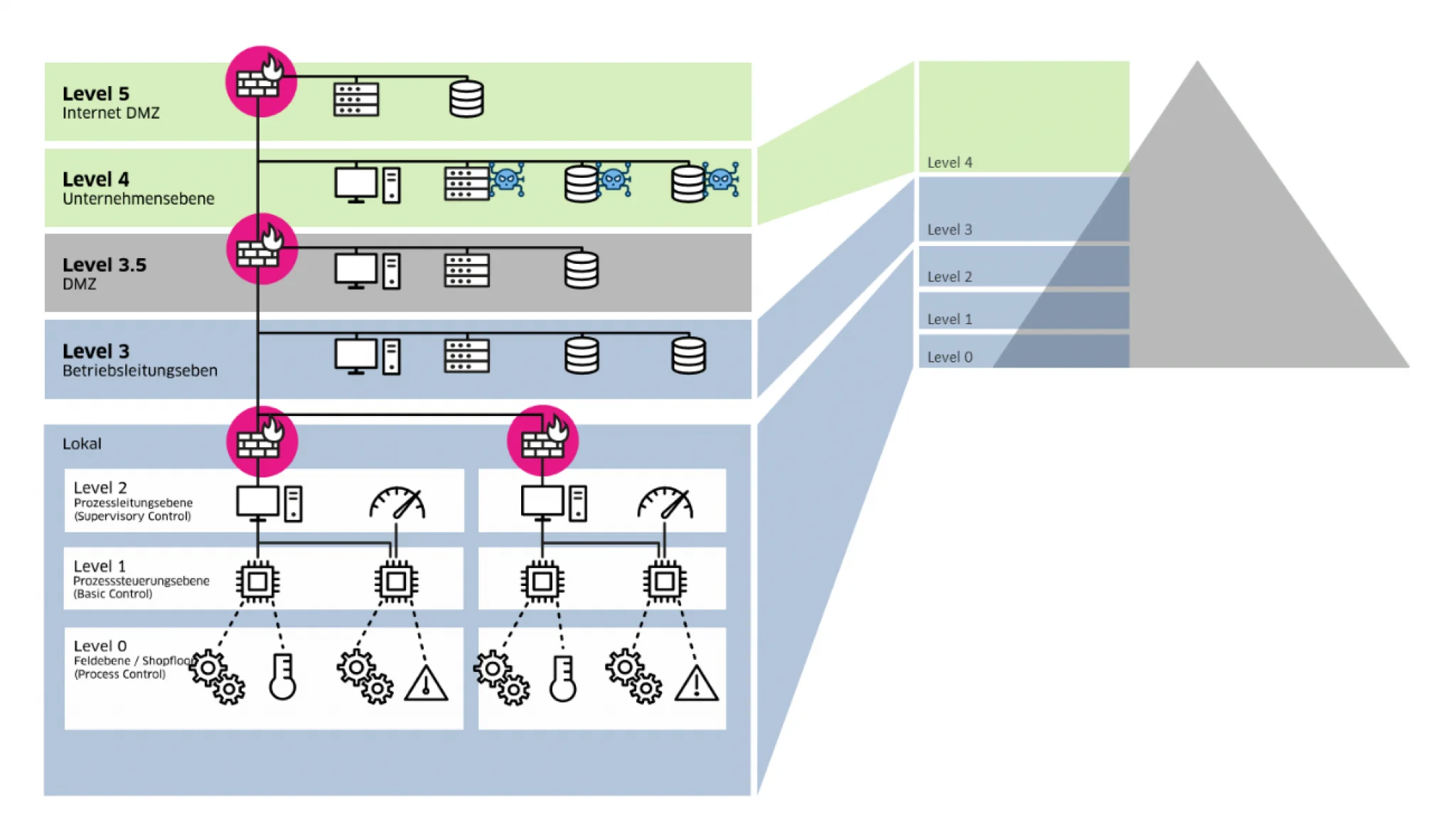
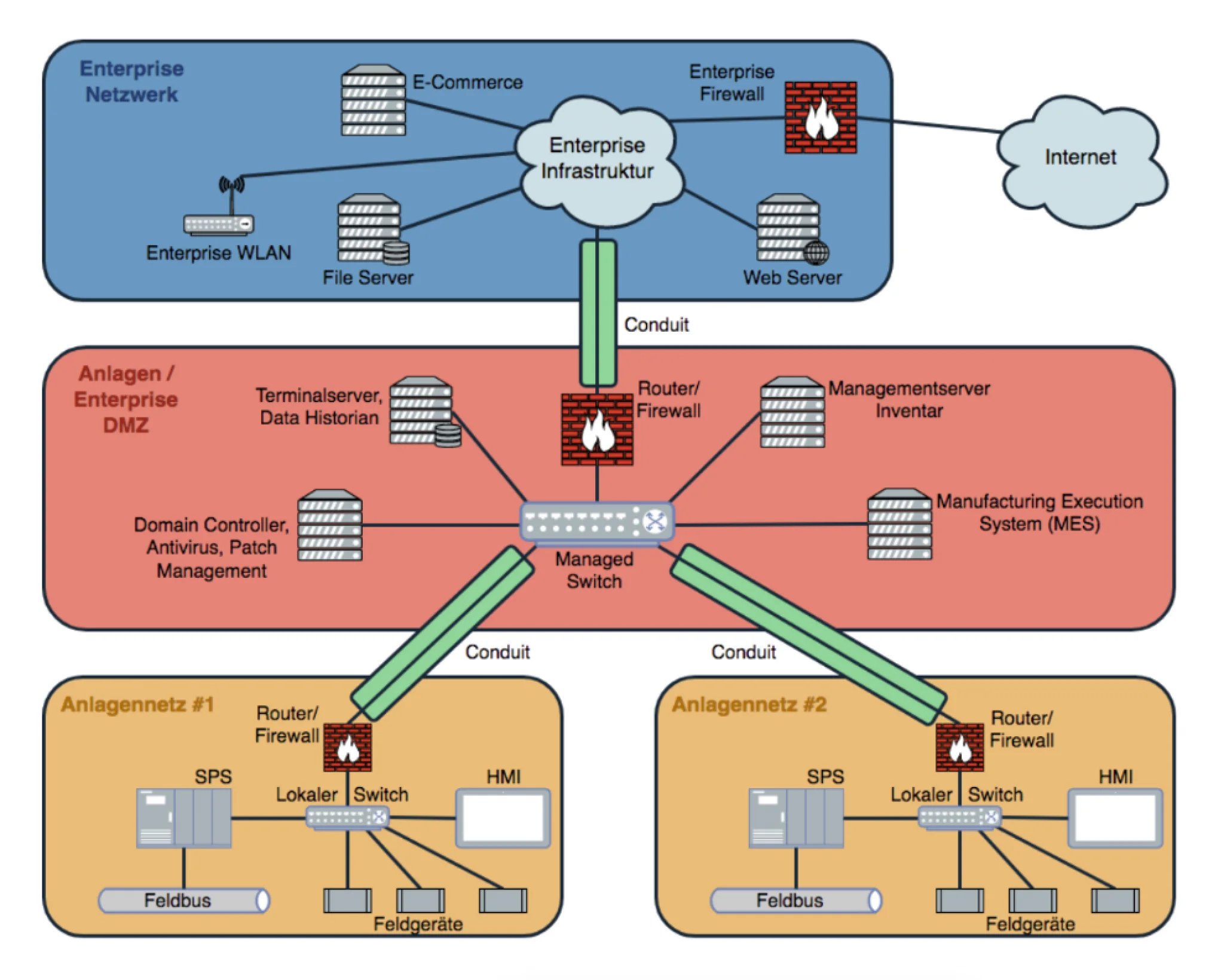
A core element of IEC 62443 is the segmentation into zones and conduits. Zones group together systems with similar security requirements, while conduits describe the communication links between these zones. This concept allows a targeted risk assessment and prevents an attacker from gaining access to the entire system with a single entry point. The standard also covers the entire life cycle - from planning and implementation to maintenance and decommissioning - and is aimed at all stakeholders involved: manufacturers, system integrators and operators.
Why do we recommend that companies use this as a guide?
The threat situation for industrial systems has changed drastically in recent years. Whereas in the past, production plants were mostly operated in isolation, today digitalization, industrial IoT and cloud connections have created numerous interfaces. Attacks such as ransomware, manipulation of process data or targeted industrial sabotage are no longer hypothetical scenarios, but real risks.
IEC 62443 provides companies with a structured approach to assess and systematically address these risks. By defining clear safety requirements, operators can:
reduce the attack surface,
ensure the availability of critical systems,
fulfill regulatory requirements (ICT, NIS2, KRITIS) and
strengthen the trust of customers, supervisory authorities and partners.
Another advantage is the international dissemination of the standard. Those who take IEC 62443 into account are not only positioning themselves in terms of safety, but also economically: compliance is explicitly required in more and more tenders.